Setting up an LDAP(S) protocol
About this task
If you use an LDAP or LDAPS directory to list your resources, in particular your personnel, you can use this directory to authenticate the Administration Center users. For more information on how to configure the keystore for LDAPS, see Configuring LDAP(S) for Talend Administration Center on Talend Help Center .
Procedure
-
On the Menu, click
Configuration and then click the
LDAP group to display the parameters.
Note that the data displayed in the capture below is used as an example, and that the field values must correspond to the values defined in your LDAP configuration.
Example
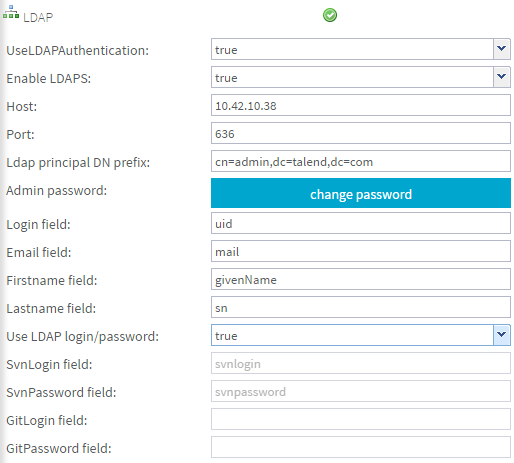
-
Set the parameters as the following:
Parameter
Value
UseLDAPAuthentication
Select true to activate LDAP authentication or false to deactivate it from the drop-down list.Information noteNote: If Personal Access Token is enabled, when LDAP Authentication is enabled or disabled, all LDAP users' Personal Access Token will be reset. For more information, see Setting up the Security Policy.Enable LDAPS
Select true to activate LDAP over SSL (LDAPS) authentication or false to deactivate it from the drop-down list.
Host
Type in the IP address and the host of the LDAP server.
Port
Type in the port of the LDAP server.
Ldap principal DN prefix
Type in the login of the user who has the right to search on the specified root or branch.
Admin password
Type in the password of the user who has the right to search on the specified root or branch.
Login field
Type in the name of the attribute representing the data that corresponds to the user's login.
The name must correspond to one of the LDAP fields defined in your LDAP configuration and the value must not be empty.
Email field
Type in the name of the attribute representing the data that corresponds to the user's Email.
The name must correspond to one of the LDAP fields defined in your LDAP configuration and the value must not be empty.
Firstname field
Type in the name of the attribute representing the data that corresponds to the user's Firstname.
The name must correspond to one of the LDAP fields defined in your LDAP configuration and the value must not be empty.
Lastname field
Type in the name of the attribute representing the data that corresponds to the user's Lastname.
The name must correspond to one of the LDAP fields defined in your LDAP configuration and the value must not be empty.
Use LDAP login/password
Select true so that Talend Administration Center credentials are used to login to SVN (deprecated)/Git. In this case, Talend Studio checks user credentials directly against the LDAP.
When setting the option to false, the previously defined mappings in the fields below are not cleared.
SvnLogin field /
GitLogin field
Type in name of the attribute representing the data that corresponds to the user's SVN (deprecated) or GIT login. This field must correspond to the field defined in your LDAP configuration.
If you use the LDAP system to handle the SVN (deprecated) and Git credentials, the recommended way is to edit these credentials through LDAP and not through the Users page as Talend Administration Center will automatically retrieve the changes done on these credentials.
SvnPassword field /
GitPassword field
Type in name of the attribute representing the data that corresponds to the user's SVN (deprecated) or GIT password. This field must correspond to the field defined in your LDAP configuration.
If you use the LDAP system to handle the SVN (deprecated) and Git credentials, the recommended way is to edit these credentials through LDAP and not through the Users page as Talend Administration Center will automatically retrieve the changes done on these credentials.
For more information on how to manage encryption of the SVN (deprecated) or Git password in LDAP for Talend Administration Center, see the documentation on Managing encryption of SVN or Git passwords in LDAP for Talend Administration Center.
Once the LDAP authentication is activated, the creation of the user account in the Users page is modified. From now on, only the Distinguished name is required as the other information about the user is retrieved from the LDAP directory. This way, user's login and password used to connect to Talend Administration Center or to Talend Studio are those defined in the LDAP directory.You can configure the LDAP connection time out by editing the value of the ldap.config.timeout property in milliseconds in the database configuration table. The defaut value is 2000.
Did this page help you?
If you find any issues with this page or its content – a typo, a missing step, or a technical error – please let us know!
